As our reliance on technology increases, more and more data surges across networks every second. Be it an email, a money transfer, or just browsing a website, data is constantly on the move. This data in motion holds immense value and needs safeguarding while in transit.
But herein lies the problem. Protecting this non-stop stream of data isn’t easy. Hackers are always on the lookout to intercept and misuse any data they can get their hands on. In addition to this, there are also accidental losses and leaks. The good news is that there are practical ways to secure your data in transit and that's precisely what we are here to share.
Our guide today takes you on a straightforward journey to understand what data in motion is and why it’s essential to keep it under lock and key. We will also discuss practical strategies to secure this moving data and share real-life stories about how organizations are tackling this important issue.
By the time you're done with this 8-minute read, you’ll have the necessary knowledge and insights to implement robust security measures for data in motion.
What Is Data In Motion? Covering The Basics
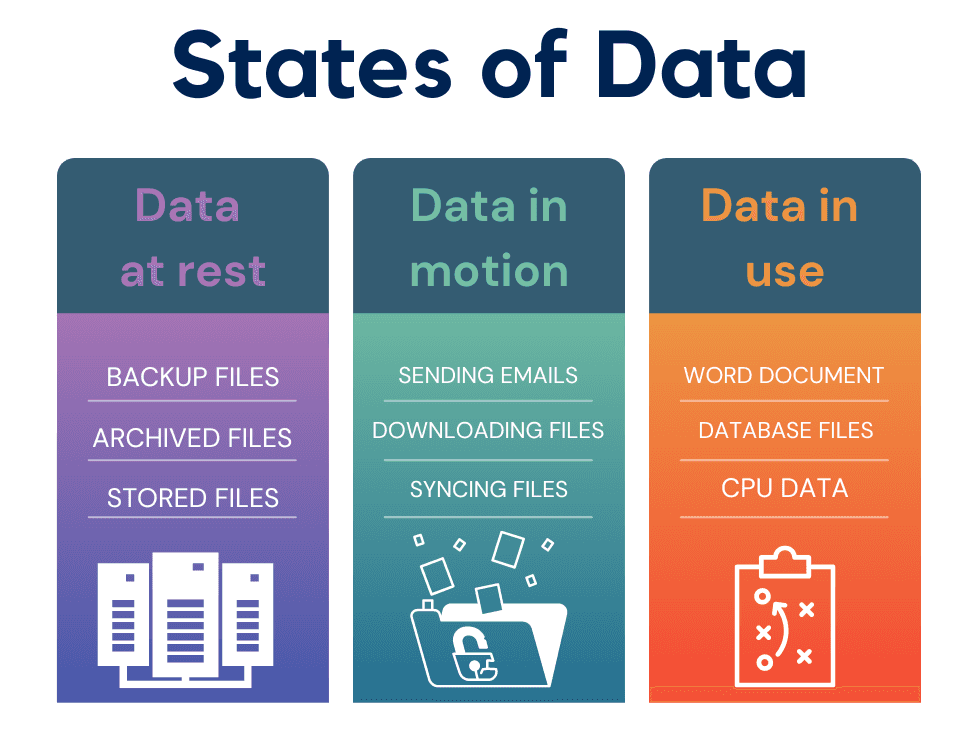
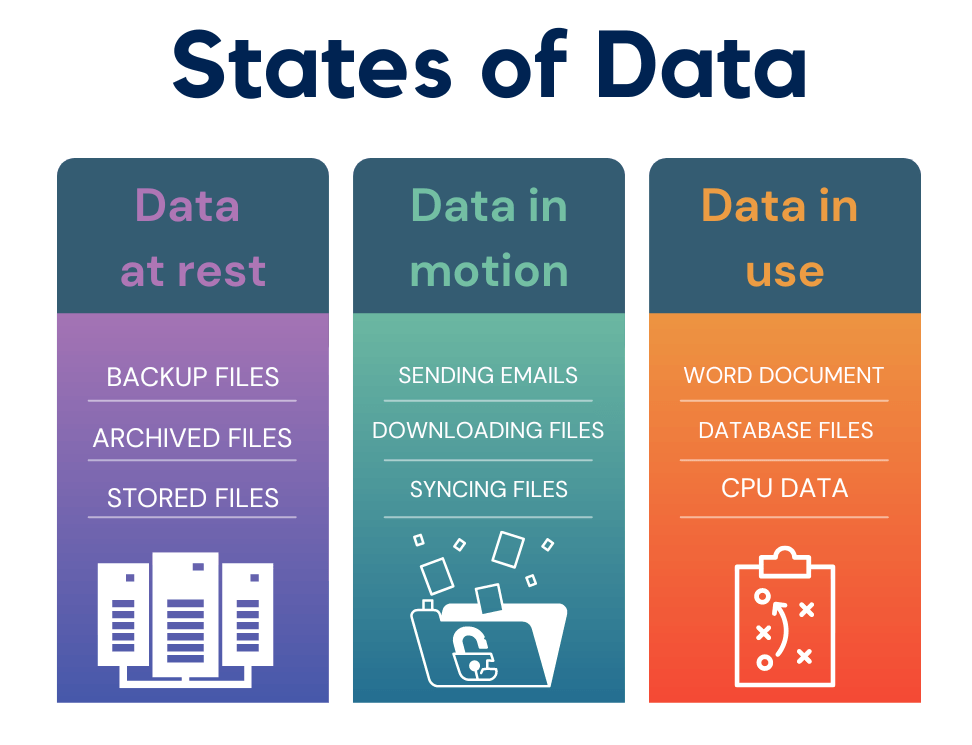
Data in motion, often termed data in transit as well, refers to the data that is actively transferred from one location to another. This could be data moving across networks like files uploaded to cloud storage or emails sent to a recipient.
To put data in motion into a better context, let's distinguish it from its counterparts.
- Data at Rest: This refers to data that is stored and not actively moving or used. Examples include files on a storage drive or data stored in a database.
- Data in Use: This is data that is currently processed or accessed. For instance, when you are analyzing data in a report or editing a document, the data is considered in use.
Securing data in motion is a critical aspect of any organization's data protection strategy. Here's why:
- Avoiding financial losses: Data breaches can cause significant financial losses because of regulatory fines, litigation costs, and loss of business.
- Prevention of data breaches: As data moves from one location to another, it becomes a prime target for cybercriminals. By securing data in motion, you can prevent unauthorized access and potential data breaches.
- Maintaining customer trust: Customers trust businesses with their personal and financial information. If this data is compromised during transmission, it causes a loss of customer trust and damage to the company's reputation.
- Compliance with regulations: Many industries have regulations that mandate the protection of data in motion. For instance, the Payment Card Industry Data Security Standard (PCI DSS) requires businesses to secure cardholder data during transmission over public or private cloud networks. Non-compliance can create hefty fines and penalties.
Now that we have grasped the concept of data in motion and understood why securing it is pivotal to any organization, let’s look at the various strategies to employ to safeguard this critical information as it traverses networks.
5 Proven Strategies To Protect Data In Motion
Securing data in motion is an imperative task for any organization. But protecting it is not a single-action task. It involves a comprehensive approach that integrates different layers of security measures.
Here are 5 strategies that are fundamental to protecting data in motion.
Encryption
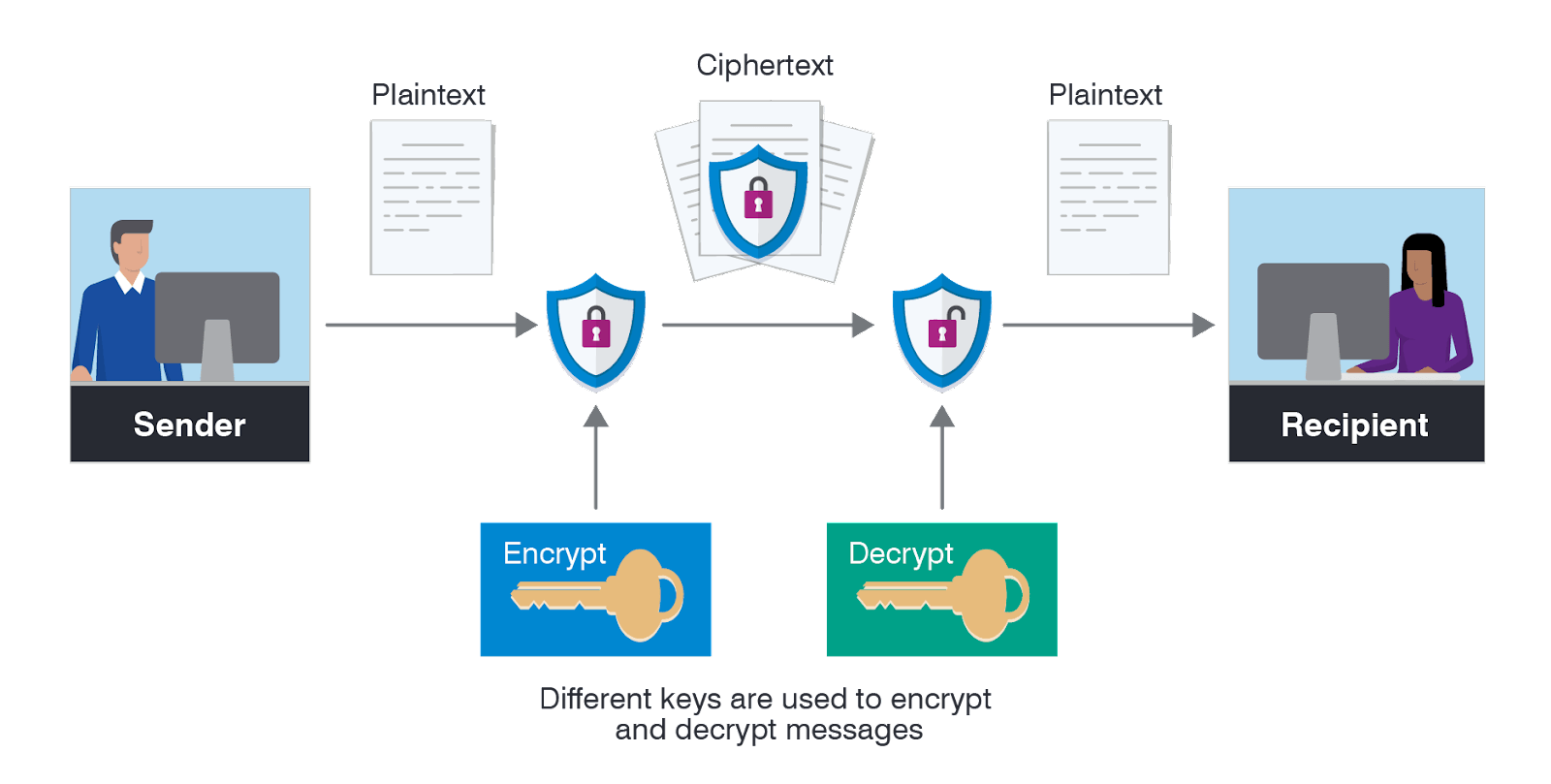
Encryption transforms data into a format that can only be deciphered with the appropriate key. This ensures that even if data is intercepted during transit, it remains unintelligible without the correct key.
By employing these encryption methods and the associated security protocols, a robust layer of protection is added to the data which ensures its confidentiality and integrity from the point of origin to the destination.
There are different encryption methods and security protocols for protecting data in motion. Some of them include:
- Asymmetric encryption: This method employs 2 distinct keys - one to encrypt data and another for its decryption. This dual-key system enhances security as possession of the encryption key alone does not enable the decryption of data.
- Internet Protocol Security (IPSec): This set of protocols encrypts each data packet during the communication process to secure Internet communication. It is frequently used to secure virtual private network tunnels, thereby providing a secure conduit for data transit.
- Transport Layer Security (TLS) and Secure Sockets Layer (SSL): These cryptographic protocols are designed to provide secure communication over a network. Commonly used to secure web browsers, email marketing, and other data transfers, these protocols function by encrypting the data before sending and then decrypting it upon receipt.
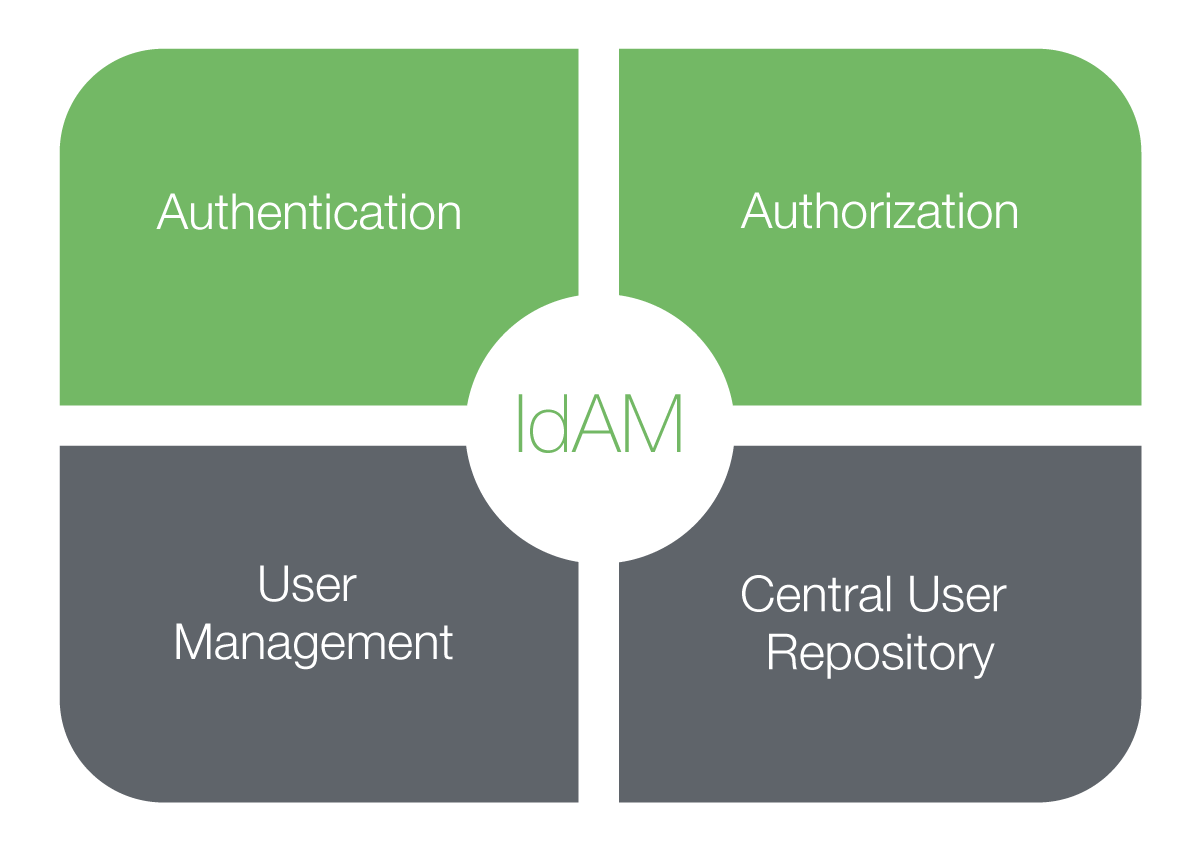
Access Control & Identity Management
Access control and identity management work to ensure that only authorized individuals can access and manipulate your data. This not only helps maintain data security but also provides a clear audit trail of data access, detailing who accessed what data and when.
Access control is all about establishing barriers to your data. It creates permissions and restrictions to ensure that only authorized users can access specific data.
This can range from simple measures such as requiring a password to access a file, to more complex strategies like establishing different access levels for various users or roles within your organization.
On the other hand, identity management is concerned with the verification of the identities of individuals attempting to access your data. This often incorporates techniques like:
- Biometric authentication: This employs unique physical or behavioral attributes, such as fingerprints, facial recognition, or voice patterns, to verify a user's identity.
- Password authentication: This is the most rudimentary form of identity management. Users are mandated to input a password to verify their identity and gain access to the data.
- Two-Factor Authentication (2FA): This enhances security by requiring users to provide two distinct types of identification. This could be a combination of something they know (like a password), or something they possess (like a mobile device).
Policy Implementation & Rule-Making
When data is transferred from one location to another, robust policies and rules should be in place. These policies act as a framework within which data transfers must operate.
One of the first steps in policy implementation is to establish clear and concise rules regarding data transfer.
- Establish restrictions on file sizes to ensure network efficiency and prevent overloading.
- Designate authorized destinations and users to minimize the risk of data exposure to unintended recipients.
- Identify the types of data that are permitted for transfer and stipulate the security measures that must be in place for each type.
Compliance with industry standards and legal regulations is also an integral part of policy implementation.
- Adhere to PCI DSS standards when handling cardholder data to secure payment information.
- Comply with HIPAA regulations to protect the confidentiality and integrity of healthcare information.
- For organizations dealing with the data of EU citizens, compliance with the General Data Protection Regulation (GDPR) is crucial.
Once you’ve set rules and are compliant, you should keep everyone on the same page. This means communicating the policies to the members of your organization. For this:
- Disseminate the policies to all relevant personnel.
- Conduct training sessions to ensure that employees are well informed about the policies and understand their roles in securing data in motion.
Lastly, don’t just set it and forget it. Given that the field of data security is continuously evolving, policies must be adaptable.
- Schedule regular reviews of the policies to ensure that they remain effective in the changing landscape.
- Update policies following technological advancements and emerging threats.
Monitoring, Tracking, & Visibility
These components are critical in establishing a secure environment for data as it travels across networks and ensuring that any anomalies are detected and addressed promptly.
Monitoring is the continuous surveillance of data as it moves through networks. It helps quickly detect and mitigate any unauthorized activities or security breaches. To set up a monitoring system in your organization:
- Implement network monitoring tools that can analyze data traffic in real time.
- Set up alerts for any suspicious or unauthorized data transfer activities which enables prompt response to potential security incidents.
Tracking enhances monitoring and provides a detailed record of data movement within and across networks. This includes information about the source, destination, and timestamps of data movement. To keep track of how data flows in your organization:
- Keep a meticulous record of data transactions, including source, destination, and timestamps.
- Utilize data loss prevention (DLP) tools that can track sensitive data and prevent unauthorized disclosure. We will discuss these in detail later.
Finally, visibility is about gaining a holistic view of the network environment in which data is moving. With full visibility, you can make decisions about security policies and measures. To increase data visibility within your organization:
- Employ network visibility solutions that offer insights into traffic patterns and data flows.
- Make sure to have a centralized dashboard where network administrators can view all data movements and assess network health.
Many modern data monitoring and tracking systems come equipped with advanced Artificial Intelligence (AI) and Machine Learning algorithms. These new systems can detect patterns or anomalies that might go unnoticed in traditional systems. This kind of intelligent analysis is invaluable in securing data in motion.
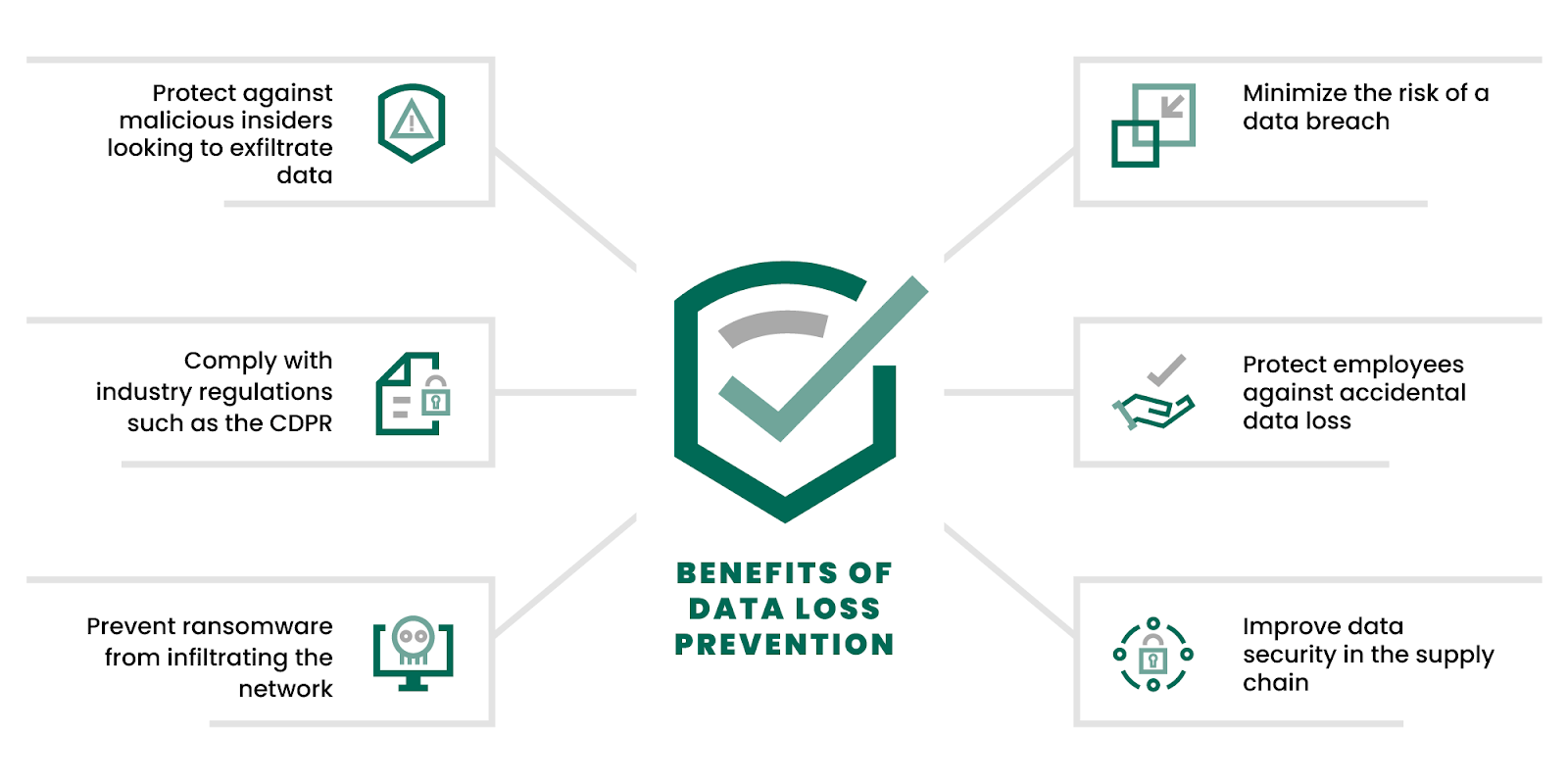
Data Loss Prevention (DLP)
Data loss prevention (DLP) is primarily aimed at stopping data from getting exposed or leaked outside the organization. While the aspects we have covered so far secure data in motion, DLP focuses on identifying and stopping the flow of sensitive information before it leaves the network.
DLP systems are adept at recognizing sensitive data, like personally identifiable information (PII), financial data, or intellectual property. This identification is crucial for classifying data based on sensitivity levels and assigning suitable protection policies to different classes of data.
A key strength of DLP systems is their ability to take real-time action.
- Blocking transmission: If the DLP system detects sensitive information being sent to unauthorized destinations, it can halt the transmission in real time.
- Masking data: In some cases, you just cannot avoid sharing data with third parties. In such cases, DLP systems can mask sensitive portions of the data, like replacing credit card numbers with asterisks.
DLP systems can even extend their protection to endpoints like laptops, mobile devices, and desktop computers. This is particularly important as data is often most at risk of exposure or leaks when accessed or handled outside the secure confines of the corporate private network.
Now let’s discuss the practical application of these methods in real-world scenarios to get a better understanding of how you can protect your in-motion data as well.
Securing Data In Motion: 2 Real-life Examples
Here are 2 real-life case studies that show how organizations are protecting their data while it’s in motion.
A Tech Manufacturer
Let’s start with the case of a leading global original design manufacturer (ODM) with operations across continents. They handle vast amounts of critical business data daily that moves between various facilities. While their at-rest data was well-protected, they recognized the unique risks associated with data in motion.
To address this, they implemented a network encryption tool. This tool:
- Complies with strict security standards.
- Requires minimal maintenance post-deployment.
- Protects sensitive data without adding operational overhead.
The tool offers:
- Compatibility with standard network equipment for easy integration.
- High-speed, secure encryption for all types of data across the network.
- Real-time low latency and near-zero overhead, ensuring network speed isn't compromised.
The results of the new implementation were significant:
- Optimized Performance: The tool did not impact latency and ensured maximum network bandwidth.
- Trusted Security: It integrated seamlessly into the existing network, securing sensitive data in transit.
A Global Logistics Company
A global logistics organization faced a challenge when its existing data security solution was phased out. They needed a new system to handle modern data protection needs.
They adopted a new data security platform that could protect data in motion, at rest, and in use. Key steps in their approach included:
- Using format-preserving tokenization to protect sensitive data across applications.
- Safely storing the relationship between tokens and credit card details for recurring payments.
The benefits they experienced were:
- Full compliance with data protection industry regulations.
- Readiness to address additional data security use cases in the future.
- Secure handling of millions of credit card details and bank account numbers.
How Estuary Can Help Secure Data In Motion
Estuary Flow is our powerhouse DataOps platform for making streaming data pipelines. Boasting real-time processing and extensive capabilities, it’s tailor-made for those looking for a reliable and efficient data movement system. Here’s how Flow helps secure data in motion.
- SOC 2 compliant: Estuary complies with this standard to secure your valuable data.
- Fault-tolerance: Flow is constructed on a fault-tolerant architecture and maintains data security and availability even if some parts of the system fail.
- Encryption: Flow offers end-to-end data encryption, and encrypts sensitive credentials you input in the web app.
- Secure connections to your systems: Use customized firewall rules or SSH tunneling to secure Flow’s connection to your sensitive databases. The approach you choose is up to you.
- Cross-region resilience: The safety features of Estuary Flow don’t stop at fault tolerance. It also operates across different regions and data centers. So even if there’s downtime in one cloud services provider, your data continues to be protected.
- Exactly-once semantics: Flow employs exactly-once semantics to ensure transactional consistency. This means your data is processed precisely one time – no more, no less. This makes sure that duplication or loss of data during transfer is avoided.
- Real-time processing: Last but not least, Flow’s real-time processing capability ensures that data is constantly on the move and not sitting vulnerable. The quicker the data moves and arrives at the destination, the lesser the chances of it being intercepted or compromised.
- Automation in schema management: When you're moving data, it's not just about getting it from point A to point B, it's also about keeping the quality intact. Estuary Flow automates schema management. This means that it takes care of organizing your data in a structured format without human intervention.
- Minimizing system load: It employs Change Data Capture (CDC) in a low-impact manner. What this means for you is that the system pulls data once and efficiently uses it across all your platforms without needing to resync. This minimizes the load on your systems, making them less prone to crashes and consequently securing your data.
Conclusion
From the simple act of sending an email to the complex data exchanges in global businesses, data in motion is everywhere, and its security should not be taken lightly. Ensuring the safety of data as it traverses between different points in a network is crucial for maintaining integrity and confidentiality.
However, securing data in motion can be a formidable challenge, especially without the right tools. This is where Estuary Flow can help. With its robust features, Flow doesn’t just provide top-notch security but also simplifies the process of protecting your data in transit.
So if you’re ready to take your data in motion security to the next level, Estuary Flow is the tool you need. You can start by signing up for Estuary Flow for free or reaching out to our team to discuss how we can meet your data-in-motion security needs.

About the author
With over 15 years in data engineering, a seasoned expert in driving growth for early-stage data companies, focusing on strategies that attract customers and users. Extensive writing provides insights to help companies scale efficiently and effectively in an evolving data landscape.
Popular Articles